
Bypassing Nemotron v3 Policy Protections
NR Labs has identified a critical policy bypass vulnerability within the NVIDIA Nemotron v3 Nano model that allows for the direct generation of sophisticated, evasive malware.
Read More






Our wide breadth of services ensures you'll get the best possible solution for your security problems.
Technical validation of your security posture provides a thorough understanding of your security priorities and meets your regulatory requirements.
Discover MoreReceive guidance on implementing and managing the cutting-edge security technologies including Artificial Intelligence and Zero Trust Architecture.
Discover MoreCyber attacks happen fast. With strategic tabletop evaluations, make sure your entire team knows how to respond when attackers show up.
Discover More




NR Labs has identified a critical policy bypass vulnerability within the NVIDIA Nemotron v3 Nano model that allows for the direct generation of sophisticated, evasive malware.
Read More
In the high-stakes theater of a cyber breach, your tools aren't the primary point of failure—your decision-making architecture is.
Read More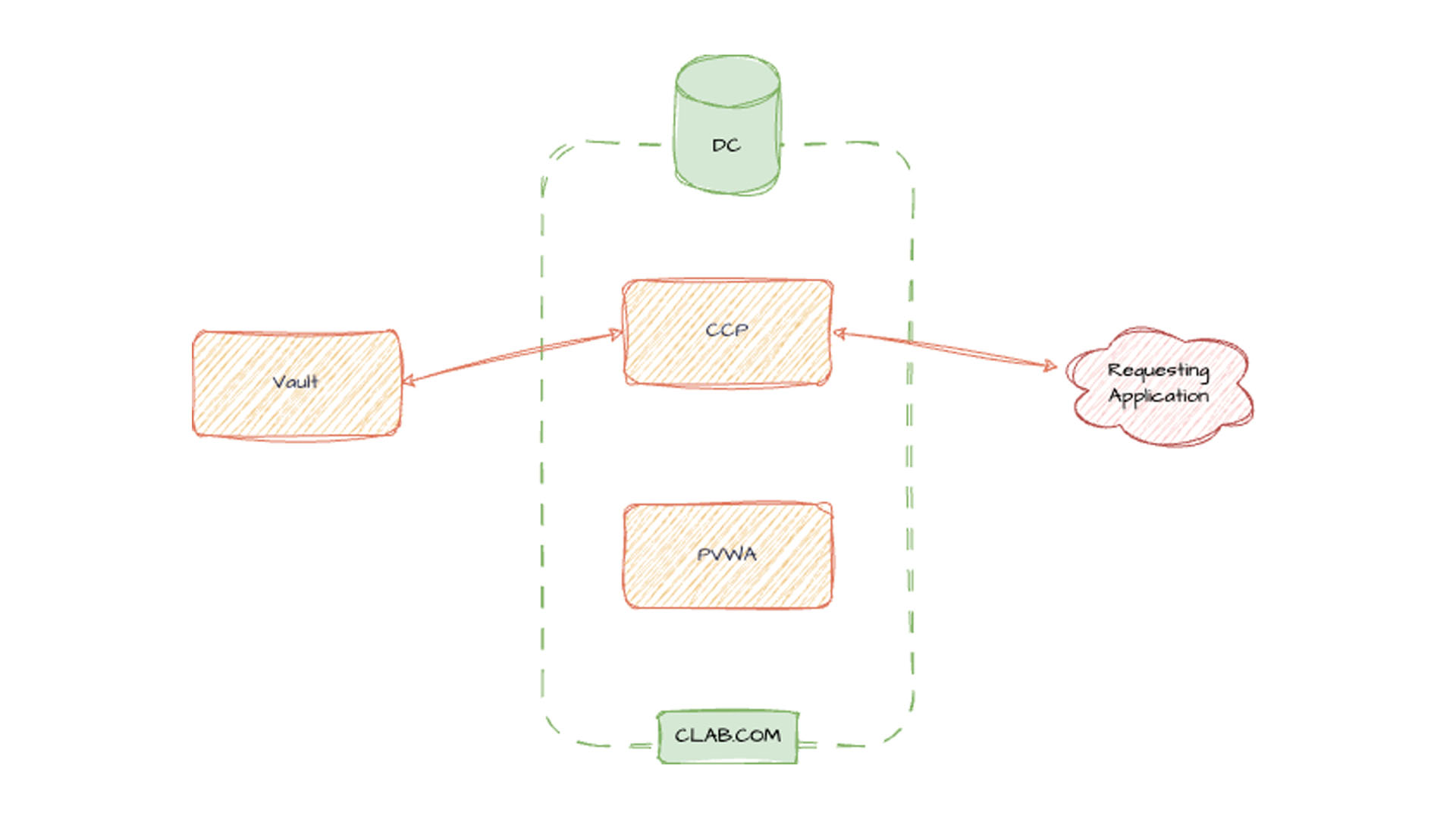
NR Labs Principal Architect Logan Zellem shares a new technical guide on the CyberArk Community blog. Explore expert insights for secure identity.
Read More